Hacking the Air Gap: Stealing Data from a Computer that isn't Connected to the Internet
Abstract
You might think that one sure-fire way to keep your computer safe from hackers is to disconnect it from the internet entirely. But did you know that even without internet, a computer can transmit data using light, sound, vibrations, or even heat? In this project, you will investigate how a spy or hacker can steal data from an "air-gapped" computer that has no internet connection. You can even use a smartphone equipped with a sensor app to demonstrate how the data can be picked up by a nearby smartphone.Summary

Objective
Investigate how an air-gapped computer can transmit data using physical quantities like light, sound, vibration, or heat, even without an internet connection.Introduction
If you read the news, you have probably read about data being hacked or stolen from computers or phones. The hacks can range from revealing embarrassing personal details to credit card numbers or contact information, and can happen to single individuals or entire companies. There are some practices you can follow to keep your data safe online, like using strong passwords, avoiding clicking on suspicious links or downloading email attachments from people you do not know, and keeping the security software on your computer up to date. But what can you do to make sure your data is completely, 100% safe? What if you disconnect your computer from the internet entirely, by physically unplugging the ethernet cable or turning off Wi-Fi? Could that prevent anyone else from accessing your data?
That might seem like an extreme measure for an average internet user. After all, most of what you use your computer for probably involves the internet. If you are not online, then you cannot play games with friends, watch movies, or use social media. But sometimes, companies and governments have extremely sensitive information (like classified military documents) or computers that control very important equipment (like a nuclear power plant). They do not want to risk those computers being hacked, so the computers are air-gapped—they are not physically connected to the rest of the internet (Figure 1). Normally, computers are connected to the internet through a router or modem via either a hardwired or wireless connection. Those routers/modems are connected to servers, which are connected to other servers...indirectly connecting millions of computers all around the world. An air-gapped computer is physically separated with no hardwired or wireless connection to the rest of the internet. It may still be part of an air-gapped network, and connected to other computers on a private network, but not the rest of the internet.
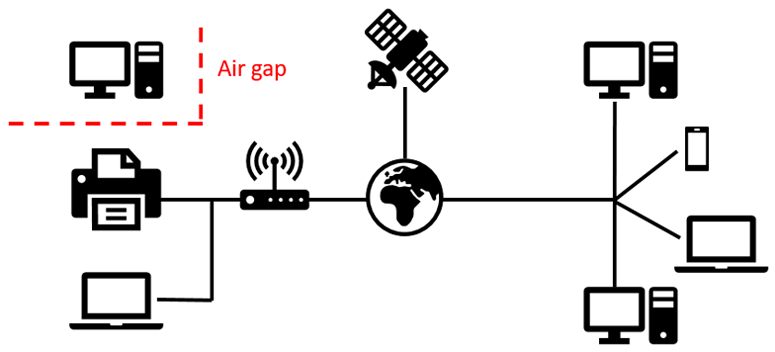 Image Credit: Ben Finio, Science Buddies / Science Buddies
Image Credit: Ben Finio, Science Buddies / Science Buddies
Figure 1. Diagram of an air-gapped computer.
So, what if you are a hacker or a government spy and you want to install malware (malicious computer software) on an air-gapped computer? How could you do it? One method involves using social engineering to trick people into inserting removable media (like a CD or USB flash drive) into the computer. This is a way to physically transport data to the computer without an internet connection, and was used to spread the Stuxnet virus in Iran (see Wired.com article in bibliography). That might be a good way to get data on to a computer, but how do you get data off the computer? What if you cannot get the USB flash drive back?
Computers send information using binary code, a series of ones and zeroes (also called on/off, high/low, or true/false). Normally, whenever you download a song, view a website, or send an email, these ones and zeroes are sent as electronic signals through a wire like an ethernet cable, or as electromagnetic waves through a connection like Wi-Fi or Bluetooth. An air-gapped computer physically lacks the means to send signals over a wired or wireless connection. However, even without an internet connection, computers still transmit signals into the world around them. They make noise, they blink lights, they vibrate, and they get hot. Light, sound, vibration, and heat are all physical quantities that we can use to send information. For example, imagine clicking a flashlight on and off to send binary code—"on" for 1, and "off" for 0. We can observe these physical quantities with our own senses like sight, sound, and touch; and we can also measure them with electronic sensors. For example:
- A thermometer measures temperature
- A photosensor measures light
- A microphone measures sound
- An accelerometer measures vibration
Many of these sensors are built into a device that most of us carry around every day—a smartphone! What if an office building has some air-gapped computers with sensitive information on them, but employees are allowed to have their personal phones in the building? If the computer can transmit a binary signal using some physical quantity that can be measured with a sensor, then the phone could record the signal. This can happen even though the phone and computer are not connected to each other through the internet. If the air-gapped computer has malware installed on it (for example, using a USB flash drive like with the Stuxnet virus, or by a disgruntled employee), it could be forced to broadcast sensitive information like secret files or passwords.
The bibliography contains a very extensive list of references that show how computers without an internet connection can transmit a signal, using a variety of physical methods and sensors (including some that were not mentioned in this introduction). In this project, you will investigate one (or more) of these methods to determine how you can send a signal from an air-gapped computer to a nearby sensor with the help of a sensor app. You will not need to write your own malware to do this—as a proof of concept, you can use controls that are built-in to your computer or operating system (for example, to change the screen brightness). You will attempt to answer questions like "What is the range of the signal?" and "Will a human using the computer notice the signal?" The exact method you pick and procedure you follow will be up to you, but the materials and procedure sections contain plenty of tips to get you started.
Terms and Concepts
- Air gap
- Network
- Malware
- Social engineering
- Removable media
- Stuxnet
- Binary
- Sensor
- Thermometer
- Photosensor
- Microphone
- Accelerometer
- Noise
- Interference
- Bit rate
Questions
- Think about people instead of computers. What are some ways that you could communicate with other people without talking? What senses would the other person use to "listen" to you?
- Use your senses to observe your computer. What can you see, feel, hear, or even smell (we do not recommend tasting your computer)? Do certain actions make the computer noisier or hotter or make the lights blink? Can you imagine how those changes could be interpreted as ones and zeroes (for example, a loud noise vs. a quiet noise)?
- Think about sensors that you encounter in everyday life. For example, your house might have a thermometer that displays the temperature. You might use a headset with a microphone to play online games with your friends. Do you think any of these sensors could measure physical changes in your computer?
Bibliography
This list provides links to many articles and publications about how data can be sent from air-gapped computers using a variety of physical methods, including some that were not discussed in the introduction. You do not need to read all of them—choose one or more specific topics that interest you to read about in more depth. Some of the links are to academic publications. It is OK if you do not understand all of the technical details in the publications. You should at least have an understanding of what physical quantity is being controlled and how it is being measured (for example, changing fan speed to change how loud the computer is, and using a microphone on a nearby smartphone to measure the noise).
- Umbelino, P. (February 2, 2017). Hacking the Aether: How Data Crosses the Air-Gap. Hackaday. Retrieved August 4, 2017.
- List, J. (August 1, 2017). Getting Data Out of Air-Gapped Networks Through the Power Cable. Hackaday. Retrieved August 4, 2017.
- Humphries, M. (June 7, 2017). xLED Malware Steals Data Using Router LEDs. PC Mag. Retrieved August 4, 2017.
- Cyber Security Research Center @ Ben-Gurion University (February 23, 2017). Cameras can Steal Data from Computer Hard Drive LED Lights. Retrieved August 4, 2017.
- Guri, M. et. al. (June 19, 2016). Fansmitter: Acoustic Data Exfiltration from (Speakerless) Air-Gapped Computers. University of the Negev Cyber Security Research Center. Retrieved August 4, 2017.
- Goodin, D. (December 2, 2013). Scientist-developed malware prototype covertly jumps air gaps using inaudible sound. Ars Technica. Retrieved August 4, 2017.
- Guri, M. et. al. (2014). AirHopper: Bridging the Air-Gap between Isolated Networks and Mobile Phones using Radio Frequencies. IEEE International Conference on Malicious and Unwanted Software (MALCON). Retrieved August 4, 2017.
- Zetter, K. (March 23, 2015). Stealing data from computers using heat. Wired. Retrieved August 4, 2017.
- Love, D. (September 27, 2013). Your Smartphone Can 'Read' What You're Typing on a Nearby Computer Simply By Detecting Keystroke Vibrations. Business Insider. Retrieved August 4, 2017.
- Zetter, K. (November 3, 2014). An Unprecedented Look at Stuxnet, the World's First Digital Weapon. Wired. Retrieved August 8, 2017.
Materials and Equipment
The materials (and software) you need for this project will depend on what physical quantity you want to measure and how you will record it. Here are some suggestions:
- Laptop or desktop computer.
- Depending on the method you choose, you might need permission to install software on the computer. Check with your teacher or librarian before using a school or library computer for this project.
- Some methods, particularly those that generate heat by running stress tests, or control the computer's cooling fans to make noise, could damage the computer if you are not careful. If you want to use these methods, try finding an old computer that you are not worried about breaking.
- Smartphone with a sensor app such as phyphox, available for free on
Google Play for Android devices (version 4.0 or newer) or from the App Store for iOS devices (iOS 9.0 or newer). Note: Phyphox does not support the light sensor on iOS devices. If you need the light sensor, you have to use Android devices for your experiment. Note that on some devices the light sensor is only updated when there is a coarse change of illuminance. This means that if the light intensity does not change or only changes slightly, the sensor appears to not record any data. The recording will continue once the light intensity changes again. If your experiments allows, it helps to wiggle the phone or the light source (e.g. flashlight) slightly to induce minimal reading fluctuations and keep the sensor active.
- If you do not use a phone, you can also purchase a variety of sensors from a vendor like Amazon.com:
- Infrared thermometer. Used to measure the temperature of a surface.
- Decibel meter. Used to measure sound levels.
- Lux meter. Used to measure light levels (not sensitive enough to detect individual LEDs, but can detect changes in screen brightness).
- Electricity usage monitor. Used to measure electrical power consumption.
- Webcam or video camera. Used to observe blinking LEDs.
Disclaimer: Science Buddies participates in affiliate programs with Home Science Tools, Amazon.com, Carolina Biological, and Jameco Electronics. Proceeds from the affiliate programs help support Science Buddies, a 501(c)(3) public charity, and keep our resources free for everyone. Our top priority is student learning. If you have any comments (positive or negative) related to purchases you've made for science projects from recommendations on our site, please let us know. Write to us at scibuddy@sciencebuddies.org.
Experimental Procedure
Cybersecurity projects can be fun, but they can also get you in trouble if you are not careful. Make sure you follow these rules when doing a cybersecurity project:
- Do not attack any individual, computer, system, or network without consent from the individual (or person who owns the computer). For example, do not try to guess someone's email password and log into their account unless you get their permission first, or try to hack into a website without permission from the owner of the website.
- Even if you have consent to perform an attack, the attack should be for learning purposes only, and you should help the individual or organization fix any problems you find (this is known as "white hat" hacking). For example, if you are able to guess someone's password, you should tell them they need to pick a stronger password (and help them learn how). Do not read their emails, change any of their account settings, look at private information or files like pictures, or tell anyone else their password.
- If your project involves human subjects, even if you have their consent, you may still need approval from your science fair or an Institutional Review Board (similar to the rules for psychology or medical experiments). See this page for more information.
- Do not pretend to be a different person, company, or other organization online. This includes pretending to be someone else on a social media site, setting up fake websites designed to look like real websites from reputable companies, or sending "phishing" or other emails designed to look like they were sent by someone else. (A controlled experiment where only study participants have access to examples of such websites or emails would be OK.)
- Do not use data that was illegally obtained (for example, contact information stolen from a company's employee database), even if it was stolen by someone else and already posted online.
- Do not publicly post sensitive personal information, even if it was obtained with consent. For example, if your project involves accessing people's contact information (legally), do not post someone's name and address in the "Results" section of your science fair display board. You should destroy any such information (by shredding paper or deleting files) when you are done with your project.
- Do not install or run any malicious software (viruses, malware, spyware, trojans, etc.) on a computer that is connected to the internet. The software could easily spread to other computers and get out of your control.
If you have any doubts or questions about your project, check with your teacher or science fair administrator before you start.
Note: You can use a smartphone equipped with a sensor app such as phyphox for many of the options in this project.
- Choose a physical quantity that you want to use to send a signal from your computer. Review the information in the background section and bibliography to help you decide.
- Find out how you will control that physical quantity on your computer. How you do this will depend on your computer and operating system. The controls could be built in to your computer's hardware (like buttons on the monitor to control the brightness) or operating system (like an icon in the taskbar to control the volume). Some quantities might require third-party software (like a program to control fan speed) or websites (like a site to play audio tones at different frequencies). If you cannot figure out how to control a certain quantity on your computer, search for help documentation online, for example "windows 10 control screen brightness." Some suggestions are provided in Table 1.
- Decide how you will measure the physical quantity. Refer to the materials section and Table 1 for a list of suggested sensors, several of which are already built in to your phone.
Warning: be extremely careful if you choose a method that could cause your computer to overheat, like running a stress test or manually controlling the cooling fans. These methods could cause permanent damage to your computer if it gets too hot.
| Quantity | How to change it | How to control it | How to measure it |
|---|---|---|---|
| Light | Blinking LEDs | Read or write large files to hard drive | Video camera |
| Screen brightness | Buttons on monitor, keyboard, or operating system taskbar | Phone equipped with a sensor app (light sensor) or lux meter | |
| Ultrasonic sound | Speakers | Website like onlinetonegenerator.com | Phone equipped with a sensor app (microphone or audio amplitude sensor) or decibel meter |
| Audible sound | Fan speed | Third-party program like SpeedFan | Phone equipped with a sensor app (microphone or audio amplitude sensor) or decibel meter |
| Vibration | Keyboard/mouse | Typing/clicking | Phone equipped with a sensor app (accelerometer) |
| Temperature | CPU or graphics card | Stress-test program like Prime95 or FurMark | Infrared thermometer |
| Electrical power | Monitor, CPU, graphics card | Screen brightness; stress-test program like Prime95 or FurMark | Electricity usage meter |
- Find out if you can send a binary signal from the computer to your sensor by changing the physical quantity you have selected. For example, if you change a computer's fan speed between 50% and 100% (do not set the fan speed to 0%, your computer will overheat!), can you detect the change while recording data with the microphone in your sensor app (audio amplitude function in phyphox)? If so, then you can send binary data, for example "1001" by setting the fan speed to either 100% (for 1) or 50% (for 0) in 1-second intervals?
- Determine the range of your signal. How far away can the sensor be? Does it require direct line-of-sight to the computer? Can it be in a different room? For example, if you are using a camera to watch an LED blink on the computer, how far away can the camera be before you can no longer see the LED?
- Examine how vulnerable your signal is to noise and interference. For example, if you are using an accelerometer to detect keyboard vibrations, what happens when people walk around the room or slam a desk drawer? If you are using a microphone to measure sound, what happens when people in the room talk?
- Figure out the bit rate of your signal, or how fast it can transmit data. How many 1's and 0's can you send per second, per minute, or per hour? For example, if you are running a CPU stress test to heat your computer up, how long does it take to notice a measurable increase in temperature of the computer's case with an infrared thermometer? How long does it take for the computer to cool back down?
- Investigate whether your signal would be detectable by a person using the computer or in the room. For example, fluctuating the monitor brightness between 0 and 100 might be very obvious to someone sitting right in front of it, but they might not notice if you change the brightness from 80 to 85. Can you send a signal that is below the threshold of human perception, but still detectable by the electronic sensor you are using?
- In order to defend against cyberattacks, you have to think like a hacker. You have just worked through how you can send a binary signal from an air-gapped computer to a nearby sensor. While you controlled the signal manually, in the real world, malware could use the signal to transmit sensitive information like passwords or classified documents. Now think on the defensive side. How could you prevent that signal from being sent or received? Imagine you are in charge of cybersecurity for a company that has sensitive information stored on air-gapped computers in an office building. What policies and procedures would you put in place to protect your air-gapped computers from cyberattacks? Is it sufficient just to bar employees from bringing their phones into the room? What if some signals can be sent through walls, or the computers are in rooms with windows? If you think dealing with these challenges sounds fun, then you might want to consider a career in cybersecurity. See the careers section to learn more.
Ask an Expert
Global Connections
The United Nations Sustainable Development Goals (UNSDGs) are a blueprint to achieve a better and more sustainable future for all.
Variations
- Choose multiple methods from the background section and compare them using the questions described in the procedure. What method has the greatest range? Which one has the fastest bit rate? Which one is least likely to be noticed by humans using the computer? Based on the answers to all your questions, if you were a hacker who wanted to steal data from an air-gapped computer, which method would you choose? If you were in charge of cybersecurity for a company or government, which method would you consider the biggest threat? How would you defend against multiple possible threats?
- In this project, you used built-in controls or third-party programs to manually control physical quantities on your computer like screen brightness or fan speed. Can you write a program in a language of your choice (Python, C++, etc.) that controls the quantity instead, and use it to transmit a binary signal? Does using software to do this allow you to transmit data faster or make the signal harder for a human to notice, for example by flickering the monitor or an LED faster than human vision can detect?
- Do this project with a friend. Have one person be the attacker and one person be the defender. The hacker should devise a way to transmit a binary signal from the computer automatically (for example, write a program to emit ultrasonic beeps that a human cannot hear). Keep this method hidden from the defender. The defender should try to discover how data is being transmitted and figure out how to prevent it. You can take turns being the attacker and defender, or use two different computers and work at the same time.
Careers
If you like this project, you might enjoy exploring these related careers:
Related Links
- Science Fair Project Guide
- Other Ideas Like This
- Pure Mathematics Project Ideas
- Science With Your Smartphone Project Ideas
- Cybersecurity Project Ideas
- My Favorites